Supplementing Network Encryption with MACsec
Written by guest author, R. Leigh Hennig from Markley Group Overview A common way to encrypt the traffic between destinations is by setting up...
1 min read
 Technium
:
Oct 9, 2023 1:20:41 PM
Technium
:
Oct 9, 2023 1:20:41 PM

Cloud computing has become mission-critical in recent years. Businesses of all sizes look to save money and improve efficiency by storing their data and applications in cloud services such as Amazon Web Services (AWS), Microsoft Azure, or Google Cloud Provider (GCP). However, this shift to the cloud comes with a new set of security challenges.
One of the biggest misconceptions about cloud security is that it's the responsibility of the cloud provider. While cloud providers do have a responsibility to secure their infrastructure, it's ultimately up to businesses to secure the data and applications that they store in the cloud.
Amazon refers to this as its “Shared Security Model” which is illustrated in this graphic.
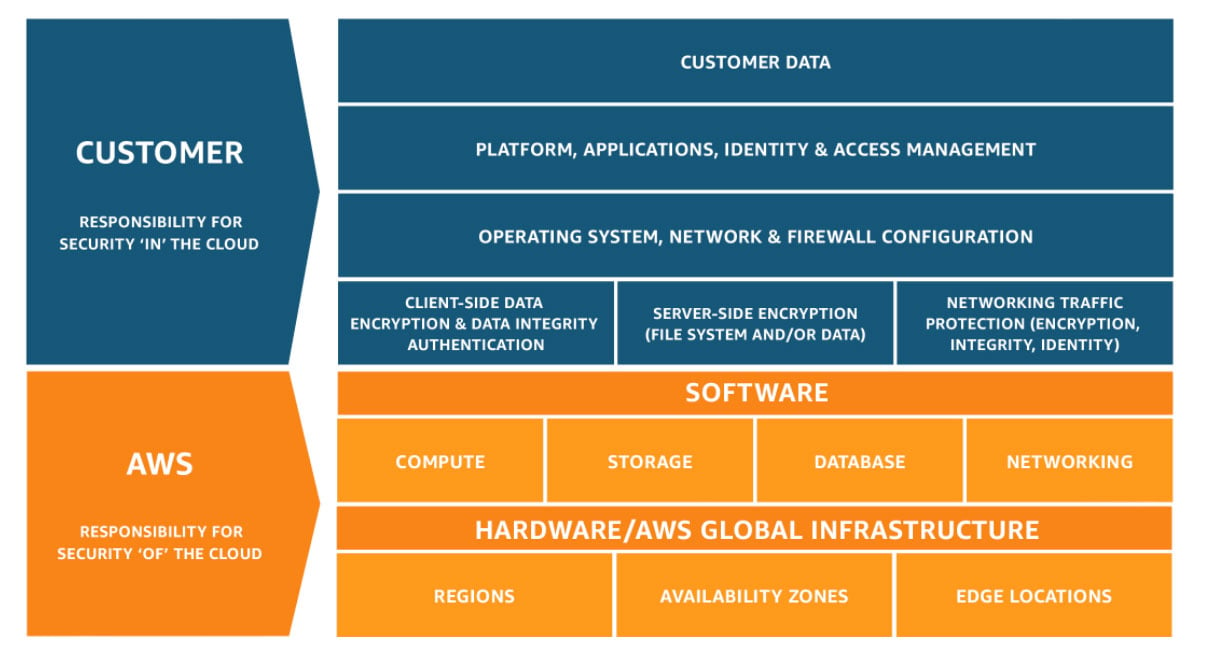
An analogy to illustrate this concept is a gated community. The outside perimeter is protected by fences, gates, and security guards, but once inside, it is up to the individual to protect their home and belongings.
There are a number of steps that businesses can take to secure their data in the cloud, including:
By taking these steps, businesses can help to protect their data from unauthorized access, use, disclosure, disruption, modification, or destruction.
In addition to these technical measures, businesses should also develop and implement a comprehensive security policy that outlines their security goals and procedures. This policy should be reviewed and updated on a regular basis to reflect changes in the threat landscape.
Cloud computing can offer a number of benefits for businesses, but it's important to remember that security is still a shared responsibility. By taking the necessary steps to secure their data in the cloud, businesses can help protect themselves from the ever-growing threat of cybercrime.
Just give us a few details and we'll be in touch.

Written by guest author, R. Leigh Hennig from Markley Group Overview A common way to encrypt the traffic between destinations is by setting up...
2 min read
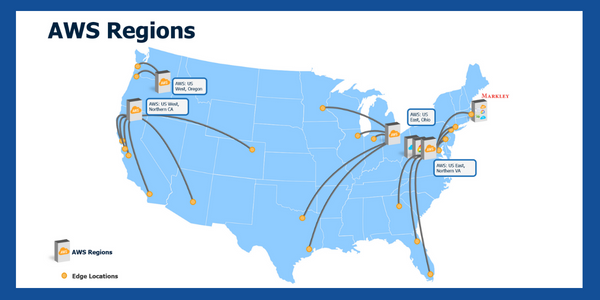
When we look at the picture above, we see the topology of the Amazon hubs and regional data centers. When you decide you...

Boston: The Evolution of Connection and Innovation