Supplementing Network Encryption with MACsec
Written by guest author, R. Leigh Hennig from Markley Group Overview A common way to encrypt the traffic between destinations is by setting up...
2 min read
 Technium
:
Apr 27, 2021 5:43:46 AM
Technium
:
Apr 27, 2021 5:43:46 AM
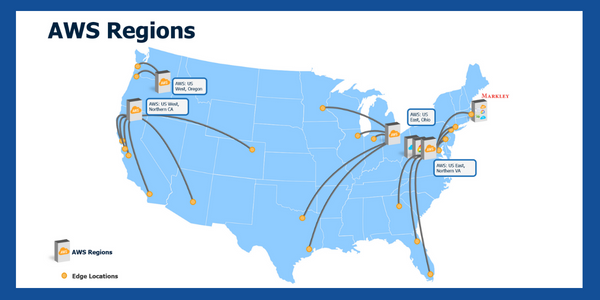
When we look at the picture above, we see the topology of the Amazon hubs and regional data centers. When you decide you want to use a server in that cloud environment (i.e., making it yours), you only get a small slice of it. There are countless others that are also connecting to their own servers in the cloud—creating a congested and potentially high latency traffic flow.
Many will purchase an unclear path from their Internet Service Provider (ISP), while others have realized they need a more predictable connection. The problem that then arises is the network; the only way you can access it is by getting to the server as fast as you can.
Here are the three ways of connecting:
1) You’re not using enough Amazon data, so you use your existing internet connection. With this, there is little to no security functionality. To enhance security, a VPN tunnel would be built to protect your data as it leaves your office and goes to the cloud environment.
2) You have Direct Connect (DX, Express Route, etc.) which limits congestion—giving you higher speed at a fixed, and typically lower, cost. Although it is private to your company and employees, it doesn’t necessarily give you a fixed path into your cloud environment or indicate where your data is going. Did you know that 90% of the time, your cloud data goes through the Markley data center? Using Direct Connect means security is designed at a single location; this often doesn’t account for remote workers or other office sites. If it does, it means data is then going from their location to the Direct Connect site to the data center and then to the cloud. Seems very cumbersome and unsecure, right?
3) You use The Fabric—giving you visibility, transparency, and the option for integrated cloud security within the data center itself, along with the ability to add other services into your single connection. The path from your location to the cloud is now secure and can easily be adjusted for the services needed by your team. Since security is in the data center, your data goes from the starting point through security measures to the desired location—providing greater security and control.
In the end, security and visibility are the top priorities when it comes to using your cloud environment; after all, it is just someone else’s data center to which you’re sending your pertinent data. Make sure the connection gives you the best value for the performance, flexibility, and resiliency that your company needs as it continues to expand.
Not sure what is right for you? Contact us for a FREE Circuit & Path Analysis to get started.

Written by guest author, R. Leigh Hennig from Markley Group Overview A common way to encrypt the traffic between destinations is by setting up...

Boston: The Evolution of Connection and Innovation

Cloud computing has become mission-critical in recent years. Businesses of all sizes look to save money and improve efficiency by storing their data...